RODCs, or Read-Only Domain Controllers, play a crucial role in optimizing Active Directory deployments, particularly in distributed environments. They provide a lightweight and secure way to extend authentication and authorization services to remote locations, ensuring seamless user access while minimizing the risk of security breaches.
RODCs offer numerous benefits, including reduced administrative overhead, improved performance, and enhanced security. By replicating only read-only data, RODCs reduce the load on primary domain controllers and minimize the impact of potential attacks. Their read-only nature also makes them an ideal choice for locations with limited connectivity or restricted network access.
Introduction to RODCs
A Read-Only Domain Controller (RODC) is a special type of domain controller in Active Directory that provides authentication and authorization services to users and computers while only storing a read-only copy of the Active Directory database. This means RODCs cannot modify the Active Directory database, making them ideal for use in branch offices or remote locations where a full-fledged domain controller is not necessary or feasible.
RODCs offer several benefits in distributed environments, particularly when dealing with limited bandwidth, security concerns, or the need for offline access.
Benefits of Using RODCs
RODCs offer numerous advantages in distributed environments, including:
- Enhanced Security: RODCs are less vulnerable to security threats since they cannot be used to modify the Active Directory database. This makes them an ideal choice for environments where security is a paramount concern.
- Reduced Bandwidth Requirements: RODCs only require a small amount of data to be replicated from the main domain controller, reducing the bandwidth requirements for communication between the main domain controller and the RODC.
- Offline Access: RODCs can provide authentication and authorization services even when the main domain controller is unavailable, ensuring continued access to resources for users and computers in the branch office or remote location.
- Improved Performance: RODCs can improve performance by reducing the load on the main domain controller, as they handle authentication and authorization requests locally.
- Simplified Management: RODCs are relatively easy to manage, as they require minimal configuration and maintenance.
Scenarios Where RODCs Are Particularly Beneficial
RODCs are particularly useful in several scenarios, including:
- Branch Offices: RODCs are ideal for branch offices that require authentication and authorization services but do not need to modify the Active Directory database. They provide a cost-effective and secure solution for these environments.
- Remote Locations: RODCs are also beneficial in remote locations where bandwidth is limited or connectivity is unreliable. They can provide offline access to resources and ensure continued operation even in the event of network outages.
- High-Security Environments: RODCs are a valuable asset in high-security environments where minimizing the risk of unauthorized modifications to the Active Directory database is crucial.
- Disaster Recovery: RODCs can serve as a backup authentication source in the event of a disaster that affects the main domain controller. This helps to ensure business continuity and minimize downtime.
RODC Functionality and Limitations
Read-only domain controllers (RODCs) are a valuable tool for extending Active Directory (AD) services to remote locations with limited connectivity. They offer several advantages, including improved performance, reduced bandwidth usage, and enhanced security. However, RODCs have specific limitations that must be understood before deploying them.
RODC Operations
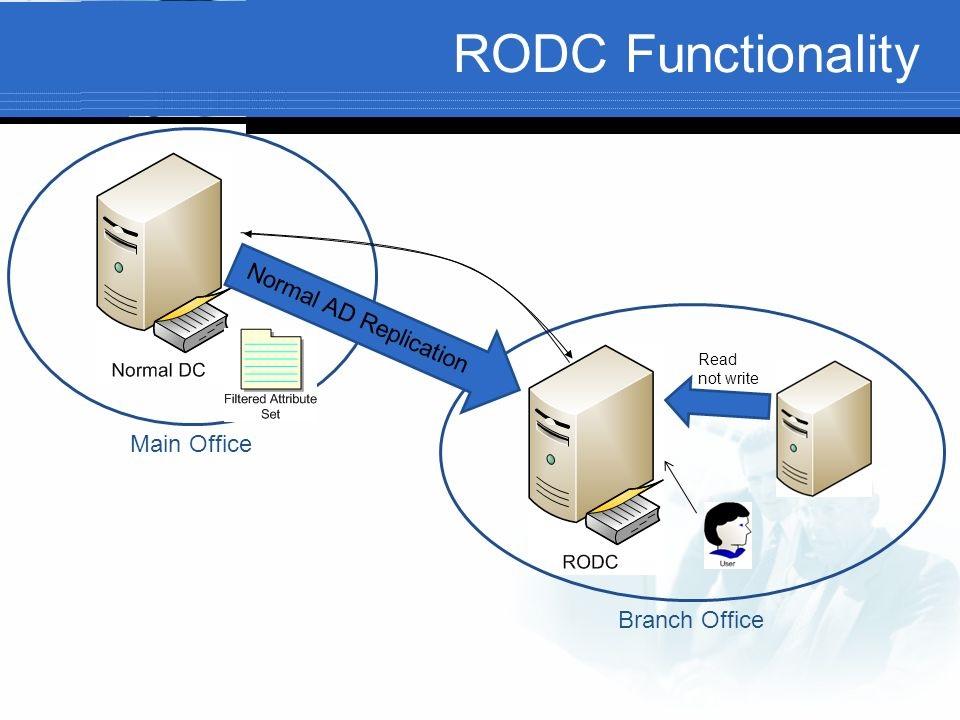
RODCs are designed to perform a subset of the operations that a standard domain controller (DC) can perform. They are primarily responsible for authenticating users and computers within their local domain, allowing users to access network resources, and providing a read-only view of the AD database. Here are some of the specific operations that RODCs can perform:
- Authentication: RODCs can authenticate users and computers against the AD database. This is their primary function and ensures users can access network resources and services.
- Read-only access to AD data: RODCs provide read-only access to the AD database, allowing users and applications to query and retrieve information. This includes user accounts, group memberships, and other directory objects.
- Group Policy processing: RODCs can process and apply Group Policy settings to users and computers within their local domain. This ensures consistent configuration and access control policies across the network.
- Kerberos ticket granting: RODCs can issue Kerberos tickets to users and computers, allowing them to access resources within the AD domain. This ensures secure communication and authentication across the network.
RODC Limitations
While RODCs provide many benefits, they also have significant limitations that impact their functionality and user experience. Understanding these limitations is crucial for successful deployment and management:
- Limited write operations: RODCs cannot perform write operations on the AD database. This means they cannot create, modify, or delete user accounts, groups, or other directory objects. This limitation is essential for maintaining data integrity and preventing unauthorized modifications to the AD database in remote locations.
- Password changes: Users cannot change their passwords directly on an RODC. Password changes must be performed on a writable domain controller, which requires a connection to the corporate network. This limitation ensures that password changes are synchronized across the entire AD domain and prevents inconsistencies in password data.
- Limited administrative tasks: RODCs cannot perform many administrative tasks, such as creating new users, managing groups, or configuring domain policies. These tasks must be performed on a writable domain controller, requiring a connection to the corporate network. This limitation is intended to prevent unauthorized modifications to the AD database and maintain central control over domain administration.
- Replication limitations: RODCs receive updates from writable domain controllers through replication. However, replication occurs less frequently than on writable domain controllers, resulting in a delay in receiving updates. This can impact the availability of the latest data on the RODC, especially for users who are frequently accessing the AD database.
Impact of Limitations on User Experience and Security
The limitations of RODCs can have a significant impact on user experience and security:
- Reduced functionality: Users cannot perform certain tasks, such as changing their passwords or creating new users, on an RODC. This can be inconvenient and require users to connect to the corporate network to perform these operations.
- Delayed data updates: Due to less frequent replication, users may not have access to the latest data on the RODC. This can lead to inconsistencies and errors, especially if users are frequently accessing the AD database.
- Enhanced security: The limited write operations and restricted administrative tasks on RODCs contribute to enhanced security. This prevents unauthorized modifications to the AD database in remote locations, ensuring data integrity and reducing the risk of security breaches.
RODC Deployment and Configuration
Deploying and configuring a Read-Only Domain Controller (RODC) is a straightforward process, but it requires careful planning and configuration to ensure it meets the specific needs of your environment. This section will cover the steps involved in deploying and configuring an RODC, explaining the different configuration options available, including replication settings, and providing guidance on choosing the appropriate configuration based on specific requirements.
Deployment Steps
Deploying an RODC involves several steps:
- Prepare the Server: The first step is to prepare the server that will host the RODC. This includes installing the necessary operating system and software, configuring the network settings, and ensuring that the server meets the minimum hardware requirements. The server must be joined to the domain and have the Active Directory Domain Services (AD DS) role installed.
- Install the RODC Role: Once the server is prepared, you can install the RODC role. This can be done using Server Manager or PowerShell. When installing the RODC role, you will need to specify the following:
- The domain that the RODC will be part of.
- The location of the RODC in the domain.
- The replication settings for the RODC.
- Configure Replication Settings: The replication settings for an RODC are crucial for ensuring that it can replicate the necessary data from the writable domain controllers (DCs). These settings include:
- The replication schedule: This determines how often the RODC will replicate data from the writable DCs.
- The replication scope: This determines which objects the RODC will replicate. By default, RODCs replicate only a subset of the Active Directory data, including user and group objects, computer objects, and security principals.
- The replication source: This specifies the writable DC that the RODC will replicate data from. The source should be a DC that is in the same site as the RODC.
- Configure the RODC for Password Replication: RODCs can be configured to replicate password hashes for users who authenticate to the RODC. This is important for scenarios where users need to authenticate to the RODC for password changes or other password-related operations. This configuration requires an administrator account that has been granted the “Replicate password hashes” permission.
- Configure the RODC for Kerberos Delegation: RODCs can be configured to delegate Kerberos authentication requests to other DCs. This is useful for scenarios where the RODC is used to authenticate clients that need to access resources on other DCs.
Configuration Options
RODCs offer several configuration options to tailor their functionality to specific needs.
- Replication Settings: As mentioned earlier, replication settings are crucial for RODC functionality. The replication schedule, scope, and source should be carefully considered based on the specific requirements of the environment. For example, in an environment with high user activity, a more frequent replication schedule may be necessary. In environments with sensitive data, it might be necessary to restrict the replication scope to only essential objects.
- Password Replication: The decision to enable password replication depends on the specific needs of the environment. If users are expected to authenticate to the RODC for password changes or other password-related operations, password replication should be enabled. However, enabling password replication can increase the security risk, as it exposes password hashes to potential attacks.
- Kerberos Delegation: Kerberos delegation is another important configuration option. If the RODC is expected to authenticate clients that need to access resources on other DCs, Kerberos delegation should be enabled. However, enabling Kerberos delegation can increase the security risk, as it allows the RODC to impersonate clients.
- Read-Only Domain Controller (RODC) Administrator Account: The RODC administrator account is a special account that has elevated privileges on the RODC. This account can be used to perform administrative tasks on the RODC, such as managing users and groups. It is important to carefully consider who should be granted RODC administrator privileges.
Choosing the Appropriate Configuration
The choice of configuration for an RODC depends on several factors, including:
- Security Requirements: If the RODC is located in a high-security environment, it is important to configure it with appropriate security settings. This may include restricting access to the RODC, disabling password replication, and limiting the replication scope.
- Performance Requirements: If the RODC is expected to handle a high volume of traffic, it is important to configure it with appropriate performance settings. This may include increasing the replication frequency and ensuring that the RODC has sufficient resources.
- Availability Requirements: If the RODC is expected to be highly available, it is important to configure it with appropriate availability settings. This may include configuring the RODC to be part of a replication group and ensuring that the RODC has a backup.
RODC Security Considerations
Read-only domain controllers (RODCs) offer a valuable solution for extending Active Directory to remote locations, but they also introduce unique security considerations. While RODCs provide a secure way to authenticate users and enforce policies in remote environments, they can be vulnerable to certain attacks if not properly secured.
Potential Vulnerabilities
RODCs are susceptible to various security threats, including:
- Password Attacks: RODCs store password hashes, which can be targeted by brute-force attacks. These attacks attempt to guess passwords by trying multiple combinations until a match is found.
- Credential Theft: Attackers may attempt to steal credentials from RODCs, such as administrator accounts, to gain unauthorized access to the domain. This can be achieved through various methods, including exploiting vulnerabilities in the operating system or applications running on the RODC.
- Data Tampering: Although RODCs are read-only, attackers could potentially modify the data on the RODC if they gain unauthorized access to the system. This could include changing user accounts, modifying group memberships, or even deleting data.
Mitigating Security Risks
Several strategies can be employed to mitigate security risks associated with RODCs:
- Strong Passwords: Implement strong password policies for all accounts, including the RODC administrator account. These policies should enforce the use of complex passwords that are difficult to guess.
- Multi-Factor Authentication: Enable multi-factor authentication (MFA) for the RODC administrator account. MFA adds an extra layer of security by requiring users to provide two or more forms of authentication, such as a password and a one-time code generated by a mobile app.
- Regular Security Updates: Keep the RODC operating system and applications up-to-date with the latest security patches. These patches address vulnerabilities that could be exploited by attackers.
- Access Control: Restrict access to the RODC to authorized personnel only. Implement access control lists (ACLs) to control who can access the RODC and what they can do.
- Network Segmentation: Isolate the RODC from the rest of the network to limit its exposure to attacks. Place the RODC on a separate subnet and configure firewalls to restrict traffic to and from the RODC.
- Security Auditing: Regularly audit the RODC for security events and suspicious activity. This can help identify potential security breaches early on and take corrective action.
Best Practices for Securing RODCs
To ensure the security of RODCs in a distributed environment, consider these best practices:
- Use a dedicated server for the RODC: Avoid installing the RODC role on a server that also hosts other applications or services. This helps to minimize the potential attack surface.
- Deploy RODCs in secure locations: Place RODCs in physically secure locations that are protected from unauthorized access.
- Use strong encryption: Configure the RODC to use strong encryption for communication with other domain controllers. This helps to protect sensitive data from eavesdropping.
- Monitor RODC activity: Use monitoring tools to track activity on the RODC and identify any suspicious behavior.
- Regularly review security settings: Regularly review the security settings on the RODC to ensure they are still appropriate.
RODC Management and Maintenance
Maintaining and managing RODCs effectively is crucial for ensuring their proper functionality and security. It involves regular monitoring, troubleshooting, and implementing appropriate security measures. This section will provide insights into various aspects of RODC management and maintenance.
Monitoring RODCs
Monitoring RODCs is essential for identifying potential issues and ensuring their optimal performance. The following methods can be employed for effective monitoring:
- Event Logs: Regularly review event logs on both the RODC and the primary domain controller (PDC) for any errors or warnings related to RODC operations. This includes events related to replication, authentication, and authorization.
- Performance Counters: Utilize performance counters to monitor the RODC’s resource utilization, including CPU, memory, and disk usage. This helps in identifying potential performance bottlenecks and resource constraints.
- Replication Status: Monitor the replication status between the RODC and the PDC. This ensures that the RODC is receiving updates from the PDC and maintaining data consistency.
- Security Auditing: Implement security auditing to track changes made to the RODC configuration, user accounts, and permissions. This helps in detecting unauthorized modifications or suspicious activities.
Troubleshooting RODC Issues
Troubleshooting RODC issues requires a systematic approach and understanding of the potential causes. Common issues include replication failures, authentication problems, and access restrictions.
- Replication Failures: Verify the network connectivity between the RODC and the PDC. Ensure that the replication ports are open and the firewall is not blocking communication. Check for any errors in the event logs related to replication.
- Authentication Problems: Examine the event logs for authentication errors. Verify that the RODC has the correct time settings and is synchronized with the PDC. Ensure that the user accounts accessing the RODC have the necessary permissions.
- Access Restrictions: Review the access control lists (ACLs) on the RODC to ensure that users have the appropriate permissions. Verify that the RODC is configured to allow the desired level of access.
Tools and Techniques for Managing RODCs
Several tools and techniques can be used to effectively manage and maintain RODCs. These include:
- Active Directory Users and Computers (ADUC): ADUC is a graphical user interface (GUI) tool that allows administrators to manage user accounts, groups, and other objects within Active Directory. It provides a centralized platform for configuring RODCs and managing their settings.
- Active Directory Domain Services (AD DS) Command-Line Tools: Command-line tools, such as dsadd, dsmod, and dsutil, offer more granular control over RODC configuration and management. These tools are useful for scripting and automating repetitive tasks.
- Group Policy Management Console (GPMC): GPMC is used to manage Group Policy Objects (GPOs) applied to RODCs. It allows administrators to control user settings, security configurations, and other policies for RODC users.
- PowerShell: PowerShell provides a powerful scripting environment for managing Active Directory, including RODCs. It offers a wide range of cmdlets for configuring, monitoring, and troubleshooting RODCs.
Common RODC Issues and Resolutions
Several common issues related to RODCs can be encountered during their management and maintenance. Here are some examples and their possible resolutions:
- Replication Lag: If the RODC experiences replication lag, it may be due to network connectivity issues, high server load, or a large volume of changes being replicated. To resolve this, check the network connection, monitor the server load, and consider increasing the replication frequency.
- Authentication Errors: Authentication errors can occur due to incorrect time settings, password policies, or user account issues. Ensure that the RODC’s time is synchronized with the PDC, verify password policies, and check the user account status.
- Limited Functionality: RODCs have limitations in functionality, such as the inability to manage user accounts or perform certain administrative tasks. Understand the limitations of RODCs and ensure that they are deployed appropriately based on the specific requirements.
RODC Integration with Other Technologies
RODCs can be integrated with other technologies to enhance security and functionality. This integration enables a more robust and flexible Active Directory environment, especially in scenarios where RODCs are deployed in remote or disconnected locations.
Integration with Active Directory Federation Services (ADFS)
ADFS is a Microsoft technology that enables secure authentication and authorization for web applications and services. Integrating RODCs with ADFS provides a secure and efficient way to manage user access to resources in a federated environment.
- Enhanced Security: By integrating RODCs with ADFS, organizations can leverage the security features of both technologies. RODCs provide offline authentication and authorization, while ADFS provides secure authentication and authorization for web applications. This combination enhances overall security for remote users.
- Simplified Management: Integrating RODCs with ADFS simplifies management tasks by centralizing authentication and authorization. Administrators can manage user accounts and permissions from a single location, regardless of the location of the RODC.
- Improved Scalability: ADFS can be deployed in a distributed manner, allowing organizations to scale their authentication and authorization infrastructure to meet growing demands. Integrating RODCs with ADFS allows organizations to extend their authentication and authorization capabilities to remote locations.
Use Cases for RODC Integration with ADFS
- Remote Branch Offices: Organizations with remote branch offices can leverage RODC integration with ADFS to provide secure access to resources for employees located in these offices. This eliminates the need for users to connect to the main Active Directory domain controller, reducing latency and improving performance.
- Cloud-Based Applications: Integrating RODCs with ADFS allows organizations to securely authenticate users accessing cloud-based applications. ADFS can act as a bridge between the on-premises Active Directory environment and the cloud, providing a single sign-on experience for users.
- Partner Integration: Organizations can integrate RODCs with ADFS to provide secure access to resources for their partners. This allows partners to access specific resources without requiring full access to the Active Directory domain.
RODC Use Cases and Best Practices
Read-only domain controllers (RODCs) offer a compelling solution for extending Active Directory (AD) services to remote locations or environments where a full-fledged domain controller might be impractical or insecure. This section delves into common use cases for RODCs, explores best practices for their effective implementation and management, and showcases real-world examples of successful RODC deployments.
Common Use Cases for RODCs
RODCs are particularly well-suited for scenarios where:
- Limited Network Connectivity: RODCs can operate in environments with intermittent or low-bandwidth network connections, enabling users to authenticate and access resources locally even when the primary domain controller is unavailable.
- Security Concerns: RODCs offer enhanced security by limiting the potential impact of a compromise. Since they do not hold the full Active Directory database, attackers cannot exploit them to gain complete control over the domain.
- Branch Offices or Remote Sites: RODCs are ideal for extending AD services to branch offices or remote sites, reducing the need for expensive and complex VPN connections or dedicated WAN links.
- Mobile Devices: RODCs can facilitate user authentication and access to resources for mobile devices that are not always connected to the corporate network.
- Disaster Recovery: RODCs can act as a backup for critical user authentication and access to resources in case of a disaster that affects the primary domain controllers.
Best Practices for Implementing and Managing RODCs
To ensure optimal performance and security, follow these best practices when implementing and managing RODCs:
- Plan for Replication: Carefully plan the replication schedule and frequency to ensure that the RODC remains up-to-date with the changes in the main domain.
- Secure the RODC: Implement robust security measures, including strong passwords, access control lists, and multi-factor authentication, to protect the RODC from unauthorized access.
- Monitor RODC Health: Regularly monitor the RODC’s performance and health to identify and address any potential issues promptly.
- Use Appropriate Delegation: Carefully delegate administrative tasks to the RODC, ensuring that only necessary permissions are granted to minimize security risks.
- Consider RODC Version: Evaluate the latest version of RODCs and their capabilities to ensure compatibility with your existing environment and future plans.
Real-World Examples of Successful RODC Deployments
- Large Retail Chain: A large retail chain deployed RODCs at each of its stores to provide local user authentication and access to critical resources, even when the corporate network was unavailable. This enabled employees to process transactions and manage inventory effectively, even in remote locations with limited connectivity.
- Global Manufacturing Company: A global manufacturing company used RODCs to extend AD services to its overseas facilities, allowing employees to access shared files and applications locally without relying on expensive VPN connections. This improved productivity and reduced network traffic.
- Educational Institution: An educational institution deployed RODCs in its remote campuses to provide students and faculty with access to campus resources, such as email, file shares, and online learning platforms. This enhanced the accessibility and convenience of the institution’s services for students and faculty located at remote campuses.
Comparison of RODCs with Other Domain Controller Types
RODCs are a specialized type of domain controller designed for specific scenarios. Understanding their differences from standard domain controllers is crucial for making informed decisions about domain controller deployment. This section will explore the key distinctions between RODCs and other domain controller types, highlighting their unique functionality, security considerations, and performance characteristics.
Functionality and Security
- RODCs are read-only domain controllers that cannot write changes to the Active Directory database. They can only read information from the database, making them suitable for scenarios where write operations are infrequent or not required.
- Standard domain controllers, on the other hand, are full-fledged domain controllers capable of both reading and writing to the Active Directory database. They are responsible for managing user accounts, group memberships, and other critical Active Directory objects.
- The read-only nature of RODCs enhances security by reducing the potential attack surface. Since they cannot modify the Active Directory database, they are less vulnerable to attacks that target write operations.
- RODCs also provide improved data integrity by preventing unauthorized modifications to the Active Directory database.
Performance
- RODCs typically have lower resource requirements compared to standard domain controllers, as they do not need to process write operations. This makes them suitable for environments with limited hardware resources.
- RODCs can also improve network performance by reducing the load on the primary domain controllers, as they can handle read requests locally.
- In scenarios where write operations are infrequent, RODCs can provide comparable performance to standard domain controllers.
Deployment and Configuration
- RODCs are typically deployed in remote or branch offices where connectivity to the primary domain controllers is limited or unreliable.
- They are also commonly used in environments with high security requirements, where limiting write access to the Active Directory database is crucial.
- Deploying RODCs involves a specific set of steps, including configuring replication schedules and establishing trust relationships with the primary domain controllers.
Choosing the Right Domain Controller Type
- For environments with high write activity and a need for full Active Directory management capabilities, standard domain controllers are the preferred choice.
- RODCs are best suited for scenarios where read-only access to Active Directory is sufficient, such as remote offices, branch offices, or environments with limited connectivity.
- When choosing between RODCs and standard domain controllers, consider factors such as network connectivity, security requirements, and performance needs.
Future of RODCs in Active Directory
The future of RODCs in Active Directory is intertwined with the evolving landscape of the technology itself. As Active Directory continues to adapt to the changing demands of modern IT environments, the role of RODCs is likely to evolve alongside.
Potential Trends and Advancements
Several trends and advancements in Active Directory could impact the usage and role of RODCs in the future. These include:
- Cloud-based Active Directory: The increasing adoption of cloud-based services like Azure Active Directory (Azure AD) could influence the role of RODCs. As organizations migrate more workloads to the cloud, the need for on-premises RODCs might diminish. However, RODCs could still play a role in hybrid scenarios, providing read-only access to data stored in Azure AD.
- Enhanced Security Features: Active Directory is constantly evolving with new security features. These advancements could potentially address some of the limitations associated with RODCs, such as their vulnerability to attacks. For example, the introduction of features like Windows Defender for Endpoint could enhance the security posture of RODCs.
- Focus on Decentralization: There is a growing trend towards decentralization in IT, with organizations moving away from centralized models. This shift could potentially lead to increased demand for RODCs, as they provide a way to distribute directory services across geographically dispersed locations.
- Increased Use of Lightweight Directory Access Protocol (LDAP): LDAP is a protocol used for accessing and managing directory services. The increasing use of LDAP could lead to greater adoption of RODCs, as they provide read-only access to directory data via LDAP.
Role of RODCs in Future Active Directory Deployments
Based on these trends, RODCs are likely to play a significant role in future Active Directory deployments, albeit in a slightly different capacity.
- Hybrid Environments: RODCs will likely continue to be valuable in hybrid environments, where organizations maintain both on-premises and cloud-based infrastructure. They can provide read-only access to on-premises Active Directory data for users and devices in the cloud.
- Branch Office Deployment: RODCs will remain a suitable option for branch office deployments, where bandwidth limitations or security concerns make it impractical to deploy a full-fledged domain controller.
- Read-Only Access for Specific Applications: RODCs can be used to provide read-only access to Active Directory data for specific applications or services, such as those that require authentication or authorization.
RODC Troubleshooting and Common Issues
Troubleshooting Read-Only Domain Controllers (RODCs) can be challenging due to their unique characteristics and limitations. Understanding common issues and their solutions is crucial for maintaining the health and functionality of RODCs within your Active Directory environment.
Common RODC Issues and Troubleshooting Steps
RODCs, while offering benefits like increased security and reduced bandwidth consumption, can present unique challenges. Here are some common issues and troubleshooting steps:
- Replication Issues: RODCs replicate changes from a writable domain controller (WDC) only when the RODC is online and the WDC is available. This can lead to stale data on the RODC, impacting user authentication or other operations.
- Troubleshooting:
- Verify the RODC is connected to the network and can communicate with the WDC.
- Check the replication status using the
repadmincommand (e.g.,repadmin /showrepl) to identify any replication errors or delays. - Ensure the replication schedule is appropriate for the RODC’s role and the expected data change frequency.
- Review the Active Directory event logs on both the RODC and the WDC for any errors related to replication.
- Troubleshooting:
- Password Synchronization Issues: RODCs can’t store all password hashes for users, relying on the WDC for password verification. This can lead to issues if the WDC is unavailable or if the password synchronization process fails.
- Troubleshooting:
- Check the password replication status using the
repadmincommand (e.g.,repadmin /showrepl) to see if the password hashes are replicated successfully. - Ensure the password replication schedule is configured appropriately for the RODC’s role and the expected user activity.
- Review the Active Directory event logs on both the RODC and the WDC for any errors related to password synchronization.
- Check the password replication status using the
- Troubleshooting:
- Authentication Issues: Users authenticating against an RODC may encounter issues if the RODC is not up-to-date with the latest user account changes or if the WDC is unavailable.
- Troubleshooting:
- Verify the RODC is connected to the network and can communicate with the WDC.
- Check the replication status using the
repadmincommand (e.g.,repadmin /showrepl) to identify any replication errors or delays. - Review the Active Directory event logs on both the RODC and the WDC for any errors related to authentication.
- Troubleshooting:
- RODC Configuration Issues: Incorrectly configuring an RODC can lead to various issues, such as insufficient permissions or improper replication settings.
- Troubleshooting:
- Review the RODC configuration using the
dsaclscommand to verify the correct permissions are set for the RODC. - Ensure the RODC is configured with the appropriate replication settings for the required data.
- Use the
repadmincommand to check the replication status and identify any configuration issues.
- Review the RODC configuration using the
- Troubleshooting:
Final Review
Understanding RODCs is essential for anyone managing a distributed Active Directory environment. By leveraging their unique capabilities, administrators can enhance security, improve performance, and simplify management tasks. As Active Directory continues to evolve, RODCs will remain a valuable tool for optimizing deployments and ensuring a secure and reliable user experience.
RODC, or Read-Only Domain Controller, is a valuable tool for organizations with geographically dispersed users. It offers a lightweight solution for authentication and basic directory services, ensuring users can access resources without relying on a full-fledged domain controller. For those looking to set up a dedicated server for online gaming, the v rising server offers a platform specifically designed for the popular survival game, V Rising.
While RODC excels in simplifying network management, the v rising server provides a dedicated environment for a unique gaming experience.
