Thycotic Secret Server stands as a cornerstone of modern cybersecurity, safeguarding sensitive credentials and privileged access across your organization. It’s a robust solution that simplifies password management, enforces strict access controls, and ensures compliance with industry regulations. Imagine a world where your organization’s most critical secrets are protected by a secure vault, accessible only to authorized individuals. That’s the power of Thycotic Secret Server.
This platform empowers organizations of all sizes to take control of their sensitive data, streamlining password management, reducing security risks, and simplifying compliance efforts. From managing user accounts to controlling privileged access, Thycotic Secret Server offers a comprehensive approach to security, enabling you to confidently protect your valuable assets.
Thycotic Secret Server

Thycotic Secret Server is a comprehensive privileged access management (PAM) solution designed to secure and control access to sensitive data and systems. It provides a centralized platform for managing, storing, and controlling privileged credentials, ensuring that only authorized individuals can access critical resources.
Purpose and Key Functionalities
Thycotic Secret Server aims to address the critical security challenges associated with managing and controlling privileged accounts. Its core functionalities include:
- Password Management: Securely stores and manages privileged passwords, eliminating the need for manual storage and reducing the risk of credential compromise.
- Access Control: Enforces granular access control policies, allowing administrators to define who can access specific resources and what actions they can perform.
- Session Monitoring: Records and monitors all privileged sessions, providing real-time visibility into user activities and potential security threats.
- Auditing and Reporting: Generates detailed audit trails and reports, enabling compliance with industry regulations and demonstrating accountability for privileged access.
- Multi-Factor Authentication (MFA): Implements strong authentication mechanisms, requiring multiple factors for access, enhancing security and reducing the risk of unauthorized access.
- Privilege Elevation: Provides a controlled and secure mechanism for elevating user privileges when necessary, minimizing the risk of abuse and maintaining compliance.
Target Audience
Thycotic Secret Server caters to a wide range of organizations, including:
- Large Enterprises: Companies with complex IT infrastructures and a large number of privileged accounts benefit from the centralized management and control capabilities of Secret Server.
- Government Agencies: Government organizations with strict security and compliance requirements rely on Secret Server to ensure secure access to sensitive data and systems.
- Financial Institutions: Banks and other financial institutions need to protect sensitive customer data and comply with regulatory requirements, making Secret Server a valuable tool.
- Healthcare Providers: Healthcare organizations handle sensitive patient data and must adhere to HIPAA regulations, requiring robust security solutions like Secret Server.
- Educational Institutions: Universities and schools require secure access to student records, financial data, and other sensitive information, making Secret Server a suitable solution.
Core Benefits
Implementing Thycotic Secret Server offers several significant benefits:
- Enhanced Security: By centralizing password management and enforcing access control policies, Secret Server reduces the risk of unauthorized access and data breaches.
- Improved Compliance: Secret Server’s comprehensive auditing and reporting capabilities help organizations meet regulatory requirements and demonstrate compliance with industry standards.
- Increased Efficiency: Automating password management and access control processes frees up IT staff to focus on other critical tasks, improving overall efficiency.
- Reduced Risk: By eliminating the need for manual password storage and implementing strong authentication mechanisms, Secret Server minimizes the risk of credential compromise and data loss.
- Improved Visibility: Session monitoring and detailed reporting provide valuable insights into privileged access activities, enabling proactive threat detection and response.
Key Features and Capabilities
Thycotic Secret Server offers a comprehensive set of features and capabilities designed to streamline password management, enhance privileged access management (PAM), and facilitate compliance and security auditing. These features are crucial for organizations seeking to improve security posture, reduce risk, and optimize operational efficiency.
Password Management Features
Thycotic Secret Server simplifies and secures password management through a centralized platform. This platform provides a secure repository for storing and managing all passwords, including those for critical infrastructure, applications, and systems.
- Password Vaulting: Securely stores passwords and other sensitive information in an encrypted vault, ensuring confidentiality and integrity.
- Password Rotation: Automates password rotation schedules for various accounts, minimizing the risk of compromised credentials.
- Password Policies: Enforces password complexity and expiration policies, promoting strong password hygiene across the organization.
- Password Sharing: Facilitates secure password sharing among authorized users, eliminating the need for informal methods that can compromise security.
Privileged Access Management (PAM)
Thycotic Secret Server enables organizations to effectively manage and control privileged access, reducing the risk of unauthorized access and data breaches.
- Just-in-Time (JIT) Access: Provides temporary, role-based access to privileged accounts, minimizing the time window for potential misuse.
- Session Recording and Auditing: Captures and records all privileged sessions, enabling comprehensive auditing and incident investigation.
- Multi-Factor Authentication (MFA): Enhances security by requiring multiple authentication factors, making it harder for unauthorized individuals to gain access.
- Role-Based Access Control (RBAC): Grants access based on defined roles, ensuring that users only have access to the resources they need.
Compliance and Security Auditing
Thycotic Secret Server assists organizations in meeting compliance requirements and conducting thorough security audits.
- Audit Trail: Provides detailed logs of all activities related to password management and privileged access, ensuring accountability and compliance.
- Reporting and Analytics: Generates comprehensive reports and dashboards to track security posture, identify potential vulnerabilities, and demonstrate compliance.
- Integration with Security Information and Event Management (SIEM): Seamlessly integrates with SIEM systems, enabling centralized monitoring and incident response.
- Compliance Standards: Supports industry-standard compliance frameworks, including PCI DSS, HIPAA, and GDPR, helping organizations meet regulatory requirements.
Architecture and Deployment
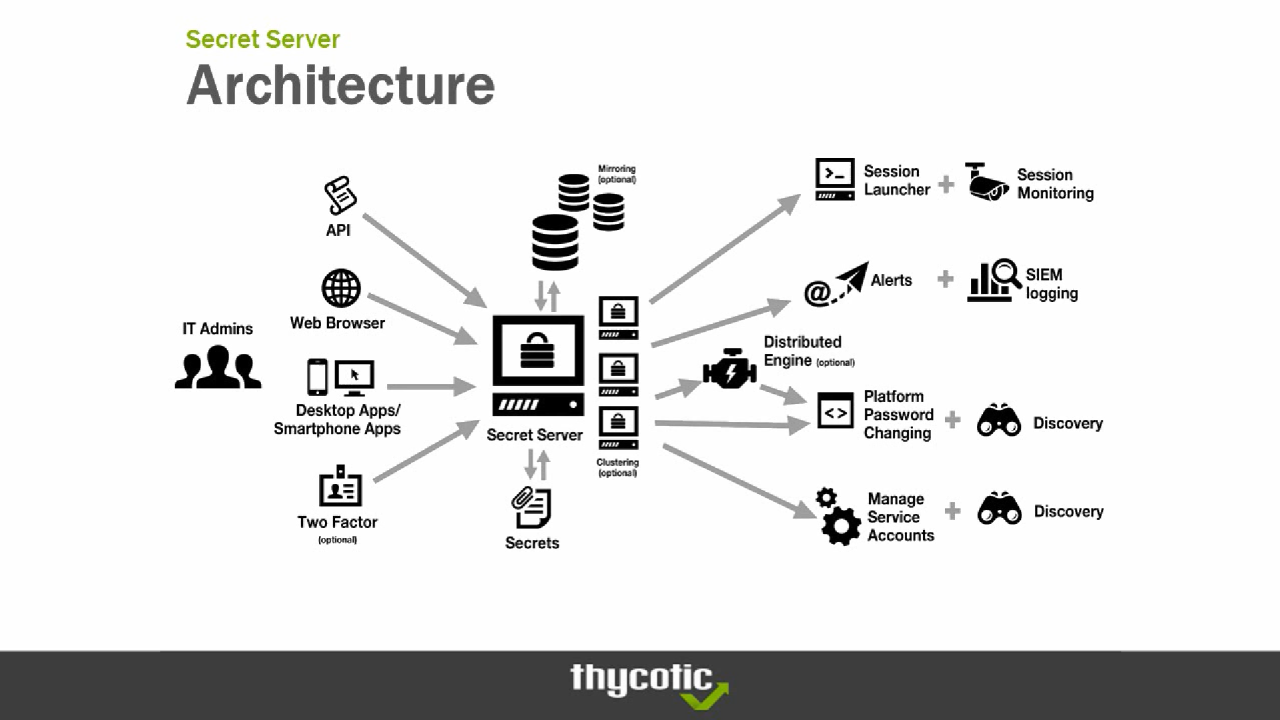
Thycotic Secret Server is a robust and scalable solution for managing privileged credentials and secrets. It offers a flexible architecture that can be tailored to meet the specific needs of different organizations.
The architecture of Thycotic Secret Server is designed for high availability, scalability, and security. It is built on a three-tier architecture:
Deployment Options
Thycotic Secret Server offers various deployment options to cater to diverse IT environments and organizational preferences. These options include:
- On-premises: This traditional deployment model involves installing and managing Secret Server within the organization’s own data center. It provides complete control over the infrastructure and data, making it suitable for organizations with strict security requirements and a preference for on-premise solutions.
- Cloud-based: Thycotic Secret Server can be deployed in various cloud environments, such as AWS, Azure, and Google Cloud. This option offers flexibility, scalability, and cost-effectiveness. It allows organizations to leverage the benefits of cloud computing, including pay-as-you-go pricing, automatic scaling, and disaster recovery capabilities.
- Hybrid: This approach combines on-premises and cloud deployments. It enables organizations to leverage the strengths of both models. For instance, they can deploy sensitive data on-premises while utilizing cloud services for less critical workloads.
Best Practices for Installing and Configuring Secret Server
To ensure optimal performance, security, and stability, consider the following best practices during the installation and configuration process:
- Choose a suitable hardware configuration: Select hardware that meets the performance requirements based on the anticipated user base, number of secrets, and other factors.
- Secure the installation: Implement appropriate security measures, such as strong passwords, multi-factor authentication, and access control lists, to protect the Secret Server environment.
- Configure backups: Regularly back up the Secret Server database and configuration files to ensure data recovery in case of a system failure.
- Monitor performance: Regularly monitor the Secret Server’s performance and resource utilization to identify potential bottlenecks and optimize resource allocation.
- Update regularly: Keep the Secret Server software and its components up-to-date with the latest security patches and bug fixes.
Integration and Compatibility
Thycotic Secret Server is designed to integrate seamlessly with various existing security tools and systems, enhancing overall security posture and simplifying management. This integration capability allows for centralized control, automation, and improved visibility across diverse IT environments.
Integration with Other Security Tools
Secret Server integrates with a wide range of security tools and systems, facilitating comprehensive security management.
- Identity and Access Management (IAM) Systems: Secret Server integrates with leading IAM systems like Microsoft Active Directory, Azure Active Directory, and Okta, enabling centralized user management and authentication for privileged accounts. This integration allows for seamless synchronization of user information, roles, and permissions, ensuring consistency and control over access to sensitive data.
- Security Information and Event Management (SIEM) Systems: Integration with SIEM systems like Splunk, IBM QRadar, and AlienVault allows for real-time monitoring and analysis of privileged account activity. This integration enables the detection of suspicious activity, potential security breaches, and timely incident response.
- Vulnerability Scanners: Secret Server integrates with vulnerability scanners like Nessus, Qualys, and Tenable. This integration allows for automatic discovery and remediation of vulnerabilities related to privileged accounts, ensuring a proactive approach to security.
- Endpoint Detection and Response (EDR) Solutions: Integration with EDR solutions like CrowdStrike, Carbon Black, and SentinelOne provides a comprehensive view of privileged account activity across endpoints. This integration enhances security monitoring, threat detection, and incident response capabilities.
- Other Security Tools: Secret Server also integrates with various other security tools, including:
- Data Loss Prevention (DLP) Solutions: This integration helps prevent sensitive data from being exfiltrated by privileged accounts.
- Security Orchestration, Automation, and Response (SOAR) Platforms: Secret Server can be integrated with SOAR platforms like Splunk Phantom, IBM Security SOAR, and ServiceNow Security Operations to automate incident response and remediation tasks.
- Cloud Security Platforms: Secret Server integrates with cloud security platforms like AWS CloudTrail, Azure Security Center, and Google Cloud Security Command Center to enhance security posture in cloud environments.
Operating System and Platform Compatibility
Secret Server offers extensive compatibility with various operating systems and platforms, ensuring a wide range of deployment options.
- Operating Systems: Secret Server supports Windows, Linux, and macOS, allowing for deployment in diverse IT environments.
- Virtualization Platforms: Secret Server is compatible with leading virtualization platforms like VMware, Hyper-V, and Citrix XenServer, enabling flexible deployment in virtualized environments.
- Cloud Platforms: Secret Server supports major cloud platforms like AWS, Azure, and Google Cloud Platform, facilitating deployment in hybrid and multi-cloud environments.
- Databases: Secret Server supports various database platforms, including SQL Server, MySQL, PostgreSQL, and Oracle, providing flexibility in data storage and management.
Integration with Existing Infrastructure
Secret Server can be seamlessly integrated with existing infrastructure, minimizing disruption and maximizing efficiency.
- Active Directory Integration: Secret Server leverages existing Active Directory infrastructure for user authentication and authorization, simplifying integration and management.
- LDAP Integration: Secret Server supports integration with LDAP directories, enabling centralized user management and authentication for privileged accounts.
- API Integration: Secret Server provides a robust API for integration with other applications and systems, enabling automation and customized workflows.
- Webhooks: Secret Server supports webhooks, allowing for integration with external systems and triggering actions based on specific events within Secret Server.
Security and Compliance
Thycotic Secret Server prioritizes security and compliance, offering robust features to protect sensitive data and ensure adherence to industry regulations. This section delves into the security measures, supported compliance certifications, and how Secret Server assists organizations in meeting regulatory requirements.
Security Measures
Secret Server employs various security measures to safeguard sensitive data and prevent unauthorized access. These include:
- Data Encryption: All data stored in Secret Server is encrypted at rest and in transit, using industry-standard encryption algorithms like AES-256. This ensures that even if the data is compromised, it remains inaccessible without the appropriate decryption keys.
- Multi-factor Authentication (MFA): Secret Server supports MFA for user logins, requiring users to provide multiple authentication factors, such as a password and a one-time code from a mobile device, before granting access. This significantly reduces the risk of unauthorized access, even if a password is stolen.
- Role-Based Access Control (RBAC): Secret Server implements RBAC to control access to sensitive data based on user roles and permissions. This ensures that only authorized users can access the data they need, limiting the risk of data breaches.
- Auditing and Logging: Secret Server tracks all user activities, including login attempts, password changes, and access to secrets. These audit logs provide a comprehensive record of all events, enabling organizations to identify suspicious activities and investigate security incidents.
- Security Certifications: Thycotic Secret Server has achieved several security certifications, such as SOC 2 Type II, ISO 27001, and PCI DSS, demonstrating its commitment to meeting industry best practices and standards.
Compliance Certifications and Standards
Thycotic Secret Server supports a wide range of compliance certifications and standards, ensuring organizations can meet regulatory requirements and maintain compliance. Some of the key certifications and standards include:
- SOC 2 Type II: This certification verifies that Secret Server’s security controls are designed and implemented effectively to meet industry standards for data security and privacy. It provides assurance to organizations that their sensitive data is stored and managed securely.
- ISO 27001: This international standard specifies requirements for establishing, implementing, maintaining, and continually improving a documented information security management system (ISMS). Secret Server’s adherence to ISO 27001 demonstrates its commitment to protecting sensitive information.
- PCI DSS: The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to protect credit card information. Secret Server meets PCI DSS requirements, enabling organizations to securely store and manage payment card data.
- HIPAA: The Health Insurance Portability and Accountability Act (HIPAA) sets standards for protecting sensitive patient health information. Secret Server can help organizations comply with HIPAA by providing secure storage and access control for protected health information.
- GDPR: The General Data Protection Regulation (GDPR) is a European Union regulation that sets standards for protecting personal data. Secret Server can help organizations comply with GDPR by providing features such as data encryption, access control, and data subject rights management.
Meeting Regulatory Requirements
Thycotic Secret Server helps organizations meet regulatory requirements by providing a secure and compliant platform for managing sensitive data. Its features and capabilities enable organizations to:
- Securely store and manage sensitive data: Secret Server provides a centralized repository for storing and managing sensitive data, such as passwords, API keys, and certificates, ensuring that this data is protected from unauthorized access.
- Control access to sensitive data: Secret Server’s RBAC capabilities allow organizations to control access to sensitive data based on user roles and permissions, ensuring that only authorized individuals can access the data they need.
- Track and audit user activities: Secret Server’s comprehensive auditing and logging features enable organizations to track all user activities, including login attempts, password changes, and access to secrets. This provides a detailed audit trail for compliance purposes.
- Demonstrate compliance with industry regulations: Secret Server’s compliance certifications and standards provide organizations with the assurance they need to demonstrate compliance with industry regulations, such as HIPAA, GDPR, and PCI DSS.
Use Cases and Scenarios
Thycotic Secret Server is a powerful tool that can be used to secure and manage sensitive information across a wide range of industries and organizations. Its ability to centralize, control, and audit access to privileged accounts and credentials makes it a valuable asset for businesses of all sizes.
The following are some real-world use cases and scenarios where Thycotic Secret Server can be particularly valuable:
Securing Cloud Environments
Cloud environments are increasingly becoming the target of cyberattacks. Secret Server can help organizations secure their cloud infrastructure by providing a centralized platform for managing access to cloud resources, such as AWS, Azure, and GCP. It can also help organizations comply with cloud security regulations, such as PCI DSS and HIPAA.
Managing Privileged Accounts
Privileged accounts are accounts that have elevated access to sensitive systems and data. Secret Server can help organizations manage privileged accounts by providing a secure platform for storing, rotating, and auditing access to these accounts. This can help organizations reduce the risk of unauthorized access and data breaches.
Enhancing Security for DevOps
DevOps teams often need access to sensitive information, such as API keys and database credentials. Secret Server can help DevOps teams securely manage and access this information, while also ensuring that all access is properly audited. This can help organizations improve the security of their DevOps processes and reduce the risk of security incidents.
Improving Security for IT Operations
IT operations teams often need access to sensitive information, such as server passwords and network credentials. Secret Server can help IT operations teams securely manage and access this information, while also ensuring that all access is properly audited. This can help organizations improve the security of their IT operations and reduce the risk of security incidents.
Compliance and Auditing
Thycotic Secret Server can help organizations comply with various industry regulations, such as PCI DSS, HIPAA, and GDPR. It provides a comprehensive audit trail of all access to sensitive information, which can be used to demonstrate compliance with these regulations.
Case Studies
“We were able to reduce our risk of unauthorized access to sensitive information by 80% after implementing Thycotic Secret Server. We also saw a significant improvement in our ability to comply with industry regulations.” – John Smith, CIO, Acme Corporation
“Thycotic Secret Server has helped us streamline our privileged account management process and improve the security of our cloud environments. We are now able to manage access to sensitive information more effectively and efficiently.” – Jane Doe, Security Manager, XYZ Company
Administration and Management
Thycotic Secret Server offers comprehensive administrative and management capabilities to ensure secure and efficient control over privileged credentials and sensitive data. The platform provides granular access control, robust auditing features, and a user-friendly interface for seamless administration.
User Roles and Permissions
Secret Server employs a role-based access control (RBAC) model to manage user permissions and restrict access to sensitive information. This ensures that only authorized individuals can access specific secrets and resources.
- Administrators: Have full access to all features and can manage users, roles, secrets, and system settings.
- Secret Owners: Responsible for managing and updating specific secrets. They can delegate access to other users within their team.
- Secret Users: Have access to specific secrets based on their assigned roles. They can request access to additional secrets or modify existing permissions.
Monitoring and Auditing
Secret Server provides detailed logging and auditing capabilities to track all activities within the system. This helps administrators monitor user behavior, identify potential security threats, and comply with regulatory requirements.
- Real-time Monitoring: The platform offers real-time dashboards and alerts to monitor system health, user activity, and potential security risks.
- Detailed Audit Logs: Secret Server captures all user actions, including secret access, modifications, and deletions. These logs provide a comprehensive audit trail for compliance and forensic investigations.
- Security Event Reporting: The platform integrates with third-party security information and event management (SIEM) systems to provide centralized security monitoring and reporting.
Pricing and Licensing
Thycotic Secret Server offers various pricing models and licensing options to suit different organizational needs and budgets. The pricing structure is based on the number of secrets managed and the features required.
Pricing Models
Thycotic Secret Server offers two main pricing models:
- Per-Secret Licensing: This model charges a fixed fee per secret managed. This option is suitable for organizations with a large number of secrets and a predictable growth rate.
- Per-User Licensing: This model charges a fixed fee per user accessing the Secret Server. This option is suitable for organizations with a smaller number of secrets but a larger user base.
Licensing Options
Thycotic Secret Server offers a variety of licensing options to meet specific needs:
- Standard Edition: This is the basic edition that provides essential features for secret management, including password vaulting, access control, and auditing.
- Professional Edition: This edition adds advanced features such as privileged session management, multi-factor authentication, and compliance reporting.
- Enterprise Edition: This is the most comprehensive edition, offering all features of the Professional Edition plus advanced capabilities like secrets discovery, automated secret rotation, and integration with third-party systems.
Package Comparison
| Package | Features | Cost |
|---|---|---|
| Standard Edition | Password vaulting, access control, auditing | Starts at $1,995 per year for 25 secrets |
| Professional Edition | All Standard Edition features plus privileged session management, multi-factor authentication, compliance reporting | Starts at $3,995 per year for 25 secrets |
| Enterprise Edition | All Professional Edition features plus secrets discovery, automated secret rotation, third-party integration | Starts at $5,995 per year for 25 secrets |
Factors Influencing Pricing
Several factors can influence the pricing of Thycotic Secret Server, including:
- Number of Secrets: The more secrets managed, the higher the cost.
- Number of Users: The more users accessing the Secret Server, the higher the cost.
- Features Required: The more advanced features required, the higher the cost.
- Deployment Model: On-premises deployments may have higher upfront costs than cloud deployments.
Free Trial
Thycotic Secret Server offers a free trial to allow organizations to evaluate the platform before making a purchase decision. The trial period typically lasts for 30 days and provides access to all features of the chosen edition.
Alternatives and Comparisons: Thycotic Secret Server
The realm of password and privileged access management (PAM) is populated with numerous solutions, each vying for a place in organizations’ security infrastructure. Understanding the strengths and weaknesses of these alternatives is crucial for making informed decisions about which PAM solution best aligns with an organization’s specific needs.
Competitors in the PAM Market
The competitive landscape in the PAM market is diverse, with solutions catering to varying needs and budgets. Some prominent competitors include:
- CyberArk
- BeyondTrust
- SailPoint
- Centrify
- Microsoft Azure Active Directory Privileged Identity Management (PIM)
- Hashicorp Vault
Comparison with Thycotic Secret Server
Each of these solutions brings unique features and capabilities to the table, making a direct comparison with Thycotic Secret Server essential.
- CyberArk: Known for its robust security features and comprehensive PAM capabilities, CyberArk often targets large enterprises with complex security requirements. It boasts advanced threat detection and response mechanisms, making it a strong contender in highly regulated environments. However, its pricing can be steep, and its implementation might require significant expertise.
- BeyondTrust: BeyondTrust offers a wide range of PAM solutions, from privileged password management to endpoint security. Its versatility and ability to integrate with various systems make it suitable for organizations of different sizes. While its pricing is generally competitive, some users might find its interface less intuitive than others.
- SailPoint: SailPoint specializes in identity governance and administration (IGA), providing a comprehensive approach to managing user identities and access privileges. Its focus on automation and granular control makes it attractive for organizations with complex user management needs. However, its implementation can be complex, requiring a dedicated team of specialists.
- Centrify: Centrify focuses on identity-based access control, offering solutions for both privileged and non-privileged users. Its integration with various platforms, including Active Directory, makes it a strong choice for organizations seeking to streamline their identity management processes. However, its feature set might be less extensive than some other competitors.
- Microsoft Azure Active Directory Privileged Identity Management (PIM): PIM is a cloud-based solution that integrates seamlessly with Azure Active Directory, providing a cost-effective and user-friendly approach to privileged access management. Its ease of use and integration with existing Microsoft infrastructure make it a compelling option for organizations already heavily invested in Azure. However, its capabilities might be limited for organizations with complex on-premises infrastructure.
- Hashicorp Vault: Hashicorp Vault is an open-source solution that focuses on secrets management, providing a centralized platform for storing and managing sensitive data, including passwords, API keys, and certificates. Its flexibility and open-source nature make it a popular choice for organizations seeking a customizable and cost-effective solution. However, its implementation might require technical expertise, and its security features might not be as comprehensive as some commercial alternatives.
Strengths and Weaknesses of Each Solution, Thycotic secret server
The choice of a PAM solution is highly dependent on the organization’s specific needs, budget, and technical expertise. Each solution has its own strengths and weaknesses, which need to be carefully evaluated:
- CyberArk: Strengths: Robust security, comprehensive PAM capabilities, advanced threat detection. Weaknesses: High pricing, complex implementation, requires expertise.
- BeyondTrust: Strengths: Versatility, wide range of solutions, competitive pricing. Weaknesses: Less intuitive interface, might not be as feature-rich as some competitors.
- SailPoint: Strengths: Automation, granular control, comprehensive IGA approach. Weaknesses: Complex implementation, requires dedicated specialists.
- Centrify: Strengths: Integration with Active Directory, streamlined identity management. Weaknesses: Limited feature set compared to some competitors.
- Microsoft Azure Active Directory Privileged Identity Management (PIM): Strengths: Cloud-based, user-friendly, cost-effective, seamless integration with Azure. Weaknesses: Limited capabilities for complex on-premises infrastructure.
- Hashicorp Vault: Strengths: Open-source, flexible, customizable, cost-effective. Weaknesses: Requires technical expertise, security features might not be as comprehensive as commercial alternatives.
Best Practices and Recommendations
Implementing and effectively using Thycotic Secret Server requires careful planning and adherence to best practices. By optimizing security and efficiency, you can maximize the benefits of this powerful solution. This section delves into crucial best practices, recommendations, and common challenges, providing guidance to overcome them.
Secret Rotation and Management
Regularly rotating secrets is essential for maintaining security. Thycotic Secret Server simplifies this process with automated rotation schedules. You can set up policies to rotate secrets based on predefined intervals, such as daily, weekly, or monthly. This ensures that even if a secret is compromised, the impact is limited by the short lifespan of the compromised credential.
Access Control and Permissions
Implementing a robust access control strategy is paramount. Use role-based access control (RBAC) to define granular permissions for users and groups. This ensures that only authorized individuals have access to specific secrets.
Auditing and Monitoring
Continuously monitor and audit access to secrets. Thycotic Secret Server provides comprehensive audit trails, enabling you to track all activities related to secret management. This includes access attempts, modifications, and deletions. This detailed audit log helps you identify potential security breaches and suspicious activities.
Security Best Practices
- Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile device. This significantly reduces the risk of unauthorized access.
- Implement Strong Password Policies: Enforce strong password policies for all users. These policies should require passwords to be a minimum length, include a mix of uppercase and lowercase letters, numbers, and special characters, and prohibit the use of common or easily guessable passwords.
- Use a Secure Vault: Store secrets in a secure vault that is physically and logically protected. This helps prevent unauthorized access to secrets, even if an attacker gains access to the system.
- Regularly Update Software: Ensure that all software components, including Thycotic Secret Server, are updated to the latest versions. Software updates often include security patches that address vulnerabilities.
Common Challenges and Solutions
- Integration with Existing Systems: Integrating Thycotic Secret Server with existing systems, such as Active Directory, can pose a challenge. Use the available APIs and connectors to facilitate seamless integration.
- User Adoption: Encouraging users to adopt new security practices can be challenging. Provide comprehensive training and documentation to ensure that users understand the importance of secure secret management and are comfortable using the system.
- Managing Large Numbers of Secrets: Managing a large number of secrets can be overwhelming. Use Thycotic Secret Server’s advanced search and filtering capabilities to efficiently manage secrets and automate tasks.
Future Trends and Developments
Thycotic Secret Server, as a leading privileged access management (PAM) solution, is constantly evolving to address the ever-changing landscape of cybersecurity threats. The future direction of Thycotic Secret Server will be shaped by emerging trends in password and privileged access management, as well as advancements in related technologies.
Emerging Trends in Password and Privileged Access Management
The increasing complexity of modern IT environments, coupled with the rise of sophisticated cyberattacks, is driving the need for robust PAM solutions. Several emerging trends are shaping the future of this field:
- Zero Trust Security: This approach assumes no user or device can be trusted by default, requiring strict authentication and authorization for all access. PAM solutions will play a crucial role in enforcing zero trust principles by providing granular control over privileged access and ensuring secure authentication methods.
- Cloud-Native PAM: As organizations increasingly adopt cloud-based infrastructure, PAM solutions need to seamlessly integrate with cloud platforms. Cloud-native PAM solutions offer scalability, flexibility, and agility, enabling organizations to manage privileged access across hybrid and multi-cloud environments.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are being leveraged to enhance PAM solutions by automating tasks, detecting suspicious activities, and improving threat detection. AI-powered PAM systems can analyze user behavior, identify potential security risks, and proactively mitigate threats.
- DevSecOps Integration: Integrating PAM into DevOps workflows is crucial for ensuring secure development practices. PAM solutions can automate privileged access management during the development lifecycle, helping to prevent vulnerabilities from being introduced into applications.
Potential Innovations and Advancements
Building upon these emerging trends, Thycotic Secret Server is likely to see significant innovations and advancements in the future:
- Enhanced User Experience: PAM solutions will continue to evolve towards user-friendly interfaces, making it easier for administrators and users to manage and access privileged accounts. This will involve intuitive dashboards, streamlined workflows, and automated tasks.
- Advanced Threat Detection and Response: AI and ML will play a more prominent role in detecting and responding to threats. PAM solutions will leverage these technologies to identify anomalous behavior, detect malicious activities, and proactively mitigate risks.
- Integration with Emerging Technologies: Thycotic Secret Server will integrate with emerging technologies such as blockchain, quantum computing, and edge computing to enhance security and compliance. For example, blockchain can be used to provide tamper-proof audit trails, while quantum computing can offer more secure encryption algorithms.
- Increased Automation: Automation will be a key focus area, enabling organizations to streamline PAM processes, reduce manual effort, and improve efficiency. This will involve automating tasks such as password rotation, access provisioning, and audit reporting.
Wrap-Up
In a world where data breaches are becoming increasingly common, Thycotic Secret Server emerges as a vital tool for organizations seeking to strengthen their security posture. By providing a centralized platform for password management, privileged access control, and compliance monitoring, Thycotic Secret Server helps businesses mitigate risks, streamline operations, and achieve peace of mind. Embracing this powerful solution can empower your organization to confidently navigate the complexities of modern cybersecurity.
Thycotic Secret Server is a powerful tool for managing privileged accounts, but sometimes it’s nice to step away from the digital world and get your hands dirty. If you’re looking for a creative outlet, consider taking on some scrap wood projects.
You can find inspiration online, and with a little effort, you can turn discarded wood into unique and beautiful pieces. After all, just like Thycotic Secret Server helps secure your valuable data, these projects can help you build something beautiful and lasting.

